More ridiculous law on the books...
Posted by Eric Stein - February 1, 2007 CE @ 05:57:55 UTC
As everyone knows, as soon as you are legally defined as a terrorist, you have no rights. Any chance you had of a fair trial is gone. Your right to a lawyer is gone. Basically, your life is over. You'd think there would be extremely stringent rules on categorizing someone as a terrorist, considering how severe the results are.
Circumstances indicating intention? Wait, aren't we defining terrorist activity here? Isn't this definition recursive?
Gathering information is a terrorist activity now? This ambiguously worded clause would make picking up a subway map and then going to home depot a terrorist activity.
Where's the presumption of innocence here? You have to prove that you didn't know? Shouldn't that be that the government has to prove you DID know?
Why doesn't anyone seem to care about the constitution anymore?
For reference, here is the full text of the Real ID act.
To the comments...(b) ENGAGE IN TERRORIST ACTIVITY DEFINED.-Section 212(a)(3)(B)(iv) of the Immigration and Nationality Act (8 U.S.C.1182(a)(3)(B)(iv)) is amended to read as follows:
(iv) ENGAGE IN TERRORIST ACTIVITY DEFINED.-
As used in this Act, the term engage in terrorist
activity means, in an individual capacity or as a
member of an organization-
(I) to commit or to incite to commit, under
circumstances indicating an intention to cause
death or serious bodily injury, a terrorist activity;
(II) to prepare or plan a terrorist activity;
(III) to gather information on potential tar-
gets for terrorist activity;
(IV) to solicit funds or other things of value
for-
(aa) a terrorist activity;
(bb) a terrorist organization described in
clause (vi)(I) or (vi)(II); or
(cc) a terrorist organization described in
clause (vi)(III), unless the solicitor can dem-
onstrate by clear and convincing evidence that
he did not know, and should not reasonably
have known, that the organization was a ter-
rorist organization;
(V) to solicit any individual-
(aa) to engage in conduct otherwise
described in this subsection;
(bb) for membership in a terrorist
organization described in clause (vi)(I) or
(vi)(II); or
(cc) for membership in a terrorist
organization described in clause (vi)(III) unless
the solicitor can demonstrate by clear and con-
vincing evidence that he did not know, and
should not reasonably have known, that the
organization was a terrorist organization; or
(VI) to commit an act that the actor knows,
or reasonably should know, affords material sup-
port, including a safe house, transportation,
communications, funds, transfer of funds or other
material financial benefit, false documentation or
identification, weapons (including chemical,
biological, or radiological weapons), explosives, or
training-
(aa) for the commission of a terrorist
activity;
(bb) to any individual who the actor
knows, or reasonably should know, has com-
mitted or plans to commit a terrorist activity;
(cc) to a terrorist organization described
in subclause (I) or (II) of clause (vi) or to
any member of such an organization; or
(dd) to a terrorist organization described
in clause (vi)(III), or to any member of such
an organization, unless the actor can dem-
onstrate by clear and convincing evidence that
the actor did not know, and should not reason-
ably have known, that the organization was
a terrorist organization.
(iv) ENGAGE IN TERRORIST ACTIVITY DEFINED.-
As used in this Act, the term engage in terrorist
activity means, in an individual capacity or as a
member of an organization-
(I) to commit or to incite to commit, under
circumstances indicating an intention to cause
death or serious bodily injury, a terrorist activity;
(II) to prepare or plan a terrorist activity;
(III) to gather information on potential tar-
gets for terrorist activity;
(IV) to solicit funds or other things of value
for-
(aa) a terrorist activity;
(bb) a terrorist organization described in
clause (vi)(I) or (vi)(II); or
(cc) a terrorist organization described in
clause (vi)(III), unless the solicitor can dem-
onstrate by clear and convincing evidence that
he did not know, and should not reasonably
have known, that the organization was a ter-
rorist organization;
(V) to solicit any individual-
(aa) to engage in conduct otherwise
described in this subsection;
(bb) for membership in a terrorist
organization described in clause (vi)(I) or
(vi)(II); or
(cc) for membership in a terrorist
organization described in clause (vi)(III) unless
the solicitor can demonstrate by clear and con-
vincing evidence that he did not know, and
should not reasonably have known, that the
organization was a terrorist organization; or
(VI) to commit an act that the actor knows,
or reasonably should know, affords material sup-
port, including a safe house, transportation,
communications, funds, transfer of funds or other
material financial benefit, false documentation or
identification, weapons (including chemical,
biological, or radiological weapons), explosives, or
training-
(aa) for the commission of a terrorist
activity;
(bb) to any individual who the actor
knows, or reasonably should know, has com-
mitted or plans to commit a terrorist activity;
(cc) to a terrorist organization described
in subclause (I) or (II) of clause (vi) or to
any member of such an organization; or
(dd) to a terrorist organization described
in clause (vi)(III), or to any member of such
an organization, unless the actor can dem-
onstrate by clear and convincing evidence that
the actor did not know, and should not reason-
ably have known, that the organization was
a terrorist organization.
Circumstances indicating intention? Wait, aren't we defining terrorist activity here? Isn't this definition recursive?
Gathering information is a terrorist activity now? This ambiguously worded clause would make picking up a subway map and then going to home depot a terrorist activity.
Where's the presumption of innocence here? You have to prove that you didn't know? Shouldn't that be that the government has to prove you DID know?
Why doesn't anyone seem to care about the constitution anymore?
For reference, here is the full text of the Real ID act.
HOPE conference in jeopardy?
Posted by Eric Stein - January 18, 2007 CE @ 10:57:30 UTC
Sad news. The HOPE conference is in danger of being discontinued after HOPE 7 in 2008 due to the venue being torn down.
That's true enough - the Hotel itself is in pretty sorry shape. I hope (pun not intended) that a new venue can be found to replace it...
Thread on the HOPE forums
To the comments...The New York City hotel that inspired the song "Pennsylvania 6-5000" will be torn down for a 2.5 million-square-foot office tower.
"I don't think anyone who has stayed there recently has been overly in love with the place... Whatever tears are going to be shed, they're too late."
"I don't think anyone who has stayed there recently has been overly in love with the place... Whatever tears are going to be shed, they're too late."
That's true enough - the Hotel itself is in pretty sorry shape. I hope (pun not intended) that a new venue can be found to replace it...
Links
nationaltrust.org story about demolitionThread on the HOPE forums
My job
Posted by Eric Stein - January 15, 2007 CE @ 11:53:19 UTC
Most jobs are to do one of these things:
1) Make computers do something they haven't done before.
2) Make computers do something that they used to do but don't do anymore.
3) Make computers stop doing something that they shouldn't be doing.
4) Figure out the cause of conditions #2 and #3.
Modified from the posting here.
To the comments...1) Make computers do something they haven't done before.
2) Make computers do something that they used to do but don't do anymore.
3) Make computers stop doing something that they shouldn't be doing.
4) Figure out the cause of conditions #2 and #3.
Modified from the posting here.
Amarok partial collection update... improved
Posted by Eric Stein - January 14, 2007 CE @ 14:20:44 UTC
I've updated my Amarok update script to fix some problems it had handling things like double quotes and parenthesis in filenames. Of course, you will probably want to change the default path...
For the old (slightly flawed in handling ugly filenames) script, see http://toba.ath.cx:724/blog/archives/amarok-collection-update-script.html
To the comments...#!/usr/bin/php
<?php
$p = '~/Media/Music/';
if (isset($argv[1]))
$p = escapeshellarg($argv[1]);
echo 'scanning ' . $p . "...\n";
$t = array();
exec('find ' . $p, $t);
foreach($t as $f)
touch($f);
system('dcop amarok collection scanCollectionChanges');
?>
<?php
$p = '~/Media/Music/';
if (isset($argv[1]))
$p = escapeshellarg($argv[1]);
echo 'scanning ' . $p . "...\n";
$t = array();
exec('find ' . $p, $t);
foreach($t as $f)
touch($f);
system('dcop amarok collection scanCollectionChanges');
?>
For the old (slightly flawed in handling ugly filenames) script, see http://toba.ath.cx:724/blog/archives/amarok-collection-update-script.html
PHP, why do you do this to me?
Posted by Eric Stein - January 14, 2007 CE @ 12:33:05 UTC
This is sort of a circuitous story, so sit tight. Quite frequently I find myself trying to use xargs to GET SOMETHING USEFUL DONE. This is not very easy to do if the strings going in are really unpleasant, such as those with spaces, quotes, and unicode.
An idea has been sitting on the back burner of my mind for awhile; a program that accepts a stream on standard in and converts each line of input into an escaped string ready to be treated as an argument. Not knowing the exact little details of how to do that with weird unicode things, I figured that php's escapeshellarg() function would probably have the exact code I wanted. PHP is open source, so this should be really easy to do, right?
It takes me all of 5 minutes to download the sourcecode (php-5.2.0.tar.bz2) and grep what I'm looking for. I find this:
Someone, somewhere (by the looks of things, Rasmus Lerdorf or Alia Alshanetsky) thought it was a good idea to do it all wrong if there's a null in the string. I go boldly forward to find out if php does indeed act weird when confronted with nulls in strings. My preliminary checks reveal the ugly truth:
Yep, that code isn't really going to work out so well for me. PHP strings can contain nulls and it's quite possible to echo them to the terminal, but the escapeshellarg() function can't handle it. While I pondered this code, I thought I saw a buffer overflow (turns out there isn't) but it encouraged me to check PHP bugs for an already reported buffer overflow in escapeshellarg(). Turns out there's another even more serious security issue in this very function. Oh wait, that bug isn't correct either. When the string is delimited with single rather than double quotes, backticks do not run commands and are treated as normal characters:
Essentially, both security issues don't exist, but the proper functionality is nonetheless broken.
To the comments...An idea has been sitting on the back burner of my mind for awhile; a program that accepts a stream on standard in and converts each line of input into an escaped string ready to be treated as an argument. Not knowing the exact little details of how to do that with weird unicode things, I figured that php's escapeshellarg() function would probably have the exact code I wanted. PHP is open source, so this should be really easy to do, right?
It takes me all of 5 minutes to download the sourcecode (php-5.2.0.tar.bz2) and grep what I'm looking for. I find this:
/*
+----------------------------------------------------------------------+
| PHP Version 5 |
+----------------------------------------------------------------------+
| Copyright (c) 1997-2006 The PHP Group |
+----------------------------------------------------------------------+
| This source file is subject to version 3.01 of the PHP license, |
| that is bundled with this package in the file LICENSE, and is |
| available through the world-wide-web at the following url: |
| http://www.php.net/license/3_01.txt |
| If you did not receive a copy of the PHP license and are unable to |
| obtain it through the world-wide-web, please send a note to |
| license@php.net so we can mail you a copy immediately. |
+----------------------------------------------------------------------+
| Author: Rasmus Lerdorf <rasmus@php.net> |
| Ilia Alshanetsky <iliaa@php.net> |
+----------------------------------------------------------------------+
*/
/* {{{ php_escape_shell_arg
*/
char *php_escape_shell_arg(char *str) {
int x, y, l;
char *cmd;
y = 0;
l = strlen(str);
cmd = safe_emalloc(4, l, 3); /* worst case */
#ifdef PHP_WIN32
cmd[y++] = '"';
#else
cmd[y++] = '\'';
#endif
for (x = 0; x < l; x++) {
switch (str[x]) {
#ifdef PHP_WIN32
case '"':
case '%':
cmd[y++] = ' ';
break;
#else
case '\'':
cmd[y++] = '\'';
cmd[y++] = '\\';
cmd[y++] = '\'';
#endif
/* fall-through */
default:
cmd[y++] = str[x];
}
}
#ifdef PHP_WIN32
cmd[y++] = '"';
#else
cmd[y++] = '\'';
#endif
cmd[y] = '\0';
return cmd;
}
/* }}} */
+----------------------------------------------------------------------+
| PHP Version 5 |
+----------------------------------------------------------------------+
| Copyright (c) 1997-2006 The PHP Group |
+----------------------------------------------------------------------+
| This source file is subject to version 3.01 of the PHP license, |
| that is bundled with this package in the file LICENSE, and is |
| available through the world-wide-web at the following url: |
| http://www.php.net/license/3_01.txt |
| If you did not receive a copy of the PHP license and are unable to |
| obtain it through the world-wide-web, please send a note to |
| license@php.net so we can mail you a copy immediately. |
+----------------------------------------------------------------------+
| Author: Rasmus Lerdorf <rasmus@php.net> |
| Ilia Alshanetsky <iliaa@php.net> |
+----------------------------------------------------------------------+
*/
/* {{{ php_escape_shell_arg
*/
char *php_escape_shell_arg(char *str) {
int x, y, l;
char *cmd;
y = 0;
l = strlen(str);
cmd = safe_emalloc(4, l, 3); /* worst case */
#ifdef PHP_WIN32
cmd[y++] = '"';
#else
cmd[y++] = '\'';
#endif
for (x = 0; x < l; x++) {
switch (str[x]) {
#ifdef PHP_WIN32
case '"':
case '%':
cmd[y++] = ' ';
break;
#else
case '\'':
cmd[y++] = '\'';
cmd[y++] = '\\';
cmd[y++] = '\'';
#endif
/* fall-through */
default:
cmd[y++] = str[x];
}
}
#ifdef PHP_WIN32
cmd[y++] = '"';
#else
cmd[y++] = '\'';
#endif
cmd[y] = '\0';
return cmd;
}
/* }}} */
Someone, somewhere (by the looks of things, Rasmus Lerdorf or Alia Alshanetsky) thought it was a good idea to do it all wrong if there's a null in the string. I go boldly forward to find out if php does indeed act weird when confronted with nulls in strings. My preliminary checks reveal the ugly truth:
eastein@glamdring:/home/eastein$ cat test.php
<?php
$a = "testing " . chr(0) . " 123";
echo $a . "\n";
echo escapeshellarg($a) . "\n";
?>
eastein@glamdring:/home/eastein$ php test.php
testing 123
'testing '
eastein@glamdring:/home/eastein$ php test.php |tr "\0" f
testing f 123
'testing '
<?php
$a = "testing " . chr(0) . " 123";
echo $a . "\n";
echo escapeshellarg($a) . "\n";
?>
eastein@glamdring:/home/eastein$ php test.php
testing 123
'testing '
eastein@glamdring:/home/eastein$ php test.php |tr "\0" f
testing f 123
'testing '
Yep, that code isn't really going to work out so well for me. PHP strings can contain nulls and it's quite possible to echo them to the terminal, but the escapeshellarg() function can't handle it. While I pondered this code, I thought I saw a buffer overflow (turns out there isn't) but it encouraged me to check PHP bugs for an already reported buffer overflow in escapeshellarg(). Turns out there's another even more serious security issue in this very function. Oh wait, that bug isn't correct either. When the string is delimited with single rather than double quotes, backticks do not run commands and are treated as normal characters:
eastein@glamdring:/home/eastein$ touch file
eastein@glamdring:/home/eastein$ ls file
file
eastein@glamdring:/home/eastein$ echo 'what`rm file`?';
what`rm file`?
eastein@glamdring:/home/eastein$ ls file
file
eastein@glamdring:/home/eastein$ echo "what`rm file`?";
what?
eastein@glamdring:/home/eastein$ ls file
ls: cannot access file: No such file or directory
eastein@glamdring:/home/eastein$
eastein@glamdring:/home/eastein$ ls file
file
eastein@glamdring:/home/eastein$ echo 'what`rm file`?';
what`rm file`?
eastein@glamdring:/home/eastein$ ls file
file
eastein@glamdring:/home/eastein$ echo "what`rm file`?";
what?
eastein@glamdring:/home/eastein$ ls file
ls: cannot access file: No such file or directory
eastein@glamdring:/home/eastein$
Essentially, both security issues don't exist, but the proper functionality is nonetheless broken.
Firewall analogy
Posted by Eric Stein - December 27, 2006 CE @ 03:58:49 UTC
I just read the best analogy to network security I've seen in a long time over at Larry Osterman's blog.
To the comments...From all accounts, the Maginot Line was a huge success. Everywhere the German army engaged the French on the Maginot line, the line did an excellent job of protecting France. But it still failed. Why? Because instead of attacking the Maginot Line head-on, the Germans instead chose to cut through where the Maginot line was weak - the Saar gap (normally an impenetrable swamp, but which was unusually dry that year) and the Low Countries (Belgium and the Netherlands, which weren't considered threats), thus bypassing the protection.
The parallels of the Maginot line and Firewalls are truly eerie. For instance, take the paragraph above, and replace the words "Maginot Line" with "firewall", "French" with "the servers", "German Army" with "Hackers", Saar gap with unforeseen cracks and "Low Countries" with "employee's laptops" and see how it works:
From all accounts, the Firewall was a huge success. Everywhere the Hackers engaged the servers on the line, the firewall did an excellent job of protecting the servers. But it still failed. Why? Because instead of attacking the Firewall head-on, the hackers instead chose to cut through where the firewall was weak - they utilized previously unforeseen cracks (because the company hadn't realized that their WEP protected network was crackable) and the employee's laptops, where the firewall was weak (because the employee's laptops weren't considered threats), thus bypassing the protection.
Very well said.The parallels of the Maginot line and Firewalls are truly eerie. For instance, take the paragraph above, and replace the words "Maginot Line" with "firewall", "French" with "the servers", "German Army" with "Hackers", Saar gap with unforeseen cracks and "Low Countries" with "employee's laptops" and see how it works:
From all accounts, the Firewall was a huge success. Everywhere the Hackers engaged the servers on the line, the firewall did an excellent job of protecting the servers. But it still failed. Why? Because instead of attacking the Firewall head-on, the hackers instead chose to cut through where the firewall was weak - they utilized previously unforeseen cracks (because the company hadn't realized that their WEP protected network was crackable) and the employee's laptops, where the firewall was weak (because the employee's laptops weren't considered threats), thus bypassing the protection.
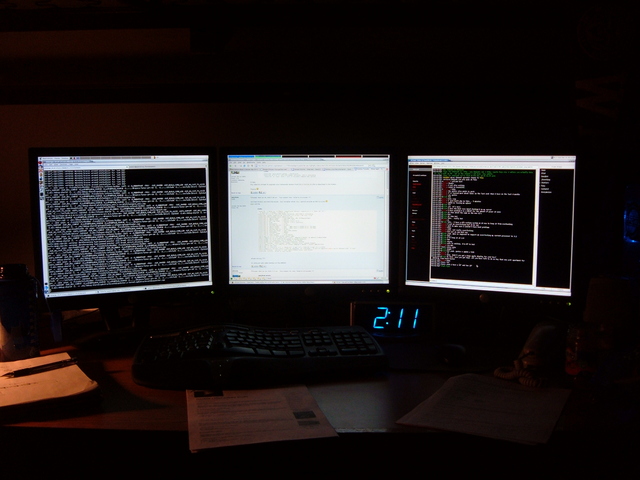
Triple monitors!
Posted by Eric Stein - December 13, 2006 CE @ 19:44:02 UTC
Triple monitors for the win. If you aren't intrigued by nvidia drivers and X.org, ignore this post.
/etc/X11/xorg.conf
Voila:
To the comments.../etc/X11/xorg.conf
Section "Files"
# For XFS (x font server), uncomment this and comment the others
# FontPath "unix/:-1"
FontPath "/usr/share/fonts/misc"
FontPath "/usr/share/fonts/util"
FontPath "/usr/share/fonts/default"
FontPath "/usr/share/fonts/default/ghostscript"
FontPath "/usr/share/fonts/75dpi"
FontPath "/usr/share/fonts/Type1"
FontPath "/usr/share/fonts/encodings"
FontPath "/usr/share/fonts/encodings/large"
FontPath "/usr/share/fonts/100dpi"
FontPath "/usr/share/fonts/corefonts"
FontPath "/usr/share/fonts/ttf-bitstream-vera"
FontPath "/usr/share/fonts/cyrillic"
EndSection
Section "Module"
SubSection "extmod"
Option "omit xfree86-dga"
EndSubSection
Load "type1"
Load "freetype"
Load "glx"
EndSection
Section "ServerFlags"
Option "blank time" "10"
Option "standby time" "20"
Option "suspend time" "30"
Option "off time" "60"
EndSection
Section "InputDevice"
Identifier "Keyboard1"
Driver "kbd"
Option "XkbModel" "microsoft"
EndSection
Section "InputDevice"
Identifier "Mouse1"
Driver "mouse"
Option "Protocol" "IMPS/2"
Option "Device" "/dev/psaux"
Option "ZAxisMapping" "4 5"
EndSection
Section "Monitor"
Identifier "Dell E193FP 0"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Monitor"
Identifier "Dell E193FP 1"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Monitor"
Identifier "Dell E193FP 2"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Device"
Identifier "nVidia GeForce6200 0"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:3:0:0"
Screen 0
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Device"
Identifier "nVidia GeForce6200 1"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:8:0:0"
Screen 0
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Device"
Identifier "nVidia GeForce6200 2"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:8:0:0"
Screen 1
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Screen"
Identifier "Screen 0"
Device "nVidia GeForce6200 0"
Monitor "Dell E193FP 0"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Screen"
Identifier "Screen 1"
Device "nVidia GeForce6200 1"
Monitor "Dell E193FP 1"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Screen"
Identifier "Screen 2"
Device "nVidia GeForce6200 2"
Monitor "Dell E193FP 2"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Server Layout"
Identifier "Multihead"
Screen "Screen 0"
Screen "Screen 1" Rightof "Screen 0"
Screen "Screen 2" Rightof "Screen 1"
InputDevice "Mouse1" "CorePointer"
InputDevice "Keyboard1" "CoreKeyboard"
Option "Xinerama" "on"
Option "Clone" "off"
EndSection
Section "DRI"
Mode 0666
EndSection
# For XFS (x font server), uncomment this and comment the others
# FontPath "unix/:-1"
FontPath "/usr/share/fonts/misc"
FontPath "/usr/share/fonts/util"
FontPath "/usr/share/fonts/default"
FontPath "/usr/share/fonts/default/ghostscript"
FontPath "/usr/share/fonts/75dpi"
FontPath "/usr/share/fonts/Type1"
FontPath "/usr/share/fonts/encodings"
FontPath "/usr/share/fonts/encodings/large"
FontPath "/usr/share/fonts/100dpi"
FontPath "/usr/share/fonts/corefonts"
FontPath "/usr/share/fonts/ttf-bitstream-vera"
FontPath "/usr/share/fonts/cyrillic"
EndSection
Section "Module"
SubSection "extmod"
Option "omit xfree86-dga"
EndSubSection
Load "type1"
Load "freetype"
Load "glx"
EndSection
Section "ServerFlags"
Option "blank time" "10"
Option "standby time" "20"
Option "suspend time" "30"
Option "off time" "60"
EndSection
Section "InputDevice"
Identifier "Keyboard1"
Driver "kbd"
Option "XkbModel" "microsoft"
EndSection
Section "InputDevice"
Identifier "Mouse1"
Driver "mouse"
Option "Protocol" "IMPS/2"
Option "Device" "/dev/psaux"
Option "ZAxisMapping" "4 5"
EndSection
Section "Monitor"
Identifier "Dell E193FP 0"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Monitor"
Identifier "Dell E193FP 1"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Monitor"
Identifier "Dell E193FP 2"
HorizSync 31.5-80
VertRefresh 75
EndSection
Section "Device"
Identifier "nVidia GeForce6200 0"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:3:0:0"
Screen 0
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Device"
Identifier "nVidia GeForce6200 1"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:8:0:0"
Screen 0
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Device"
Identifier "nVidia GeForce6200 2"
VendorName "XFX"
Driver "nvidia"
BusID "PCI:8:0:0"
Screen 1
Option "NoLogo"
Option "UseDisplayDevice" "DFP"
Option "RenderAccel" "true"
Option "AllowGLXWithComposite" "true"
Option "UseEdidDpi" "FALSE"
EndSection
Section "Screen"
Identifier "Screen 0"
Device "nVidia GeForce6200 0"
Monitor "Dell E193FP 0"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Screen"
Identifier "Screen 1"
Device "nVidia GeForce6200 1"
Monitor "Dell E193FP 1"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Screen"
Identifier "Screen 2"
Device "nVidia GeForce6200 2"
Monitor "Dell E193FP 2"
DefaultDepth 24
SubSection "Display"
Depth 24
Modes "1280x1024"
EndSubsection
EndSection
Section "Server Layout"
Identifier "Multihead"
Screen "Screen 0"
Screen "Screen 1" Rightof "Screen 0"
Screen "Screen 2" Rightof "Screen 1"
InputDevice "Mouse1" "CorePointer"
InputDevice "Keyboard1" "CoreKeyboard"
Option "Xinerama" "on"
Option "Clone" "off"
EndSection
Section "DRI"
Mode 0666
EndSection
Voila:
Myers-Briggs
Posted by Eric Stein - December 11, 2006 CE @ 09:20:23 UTC
Evidently, I'm ENTJ.
To the comments...ENTJ - Business executives, CEOs, organization founders, business administrators, managers, entrepeneurs, judges, lawyers, computer consultants, university professors, politicians, credit investigators, labor relations worker, marketing department manager, mortgage banker, systems analysts, scientists. They are born to lead and can steer the organization towards their vision, using their excellent organizing and understanding of what needs to get done.
I guess I do like to split hairs while arguing about computers... that qualifies me for a few of these professions at least.I guess hardware isn't so bad after all
Posted by Eric Stein - December 10, 2006 CE @ 04:08:11 UTC
It all began so suddenly on October 30. I'm reading a textbook on my bed before class and suddenly my computer reboots.
At this point, I still had no money and now no computer. My paycheck was still a ways off. So, I stumbled along with my laptop for a few weeks. By the way, said laptop's window manager killed itself violently when I used portupgrade, so I was using TWM. TWM sucks. TWM sucks more than you can possibly imagine. It's ugly, it has the bare minimum of functionality, and did I mention that it's ugly? Behold, how ugly it truly is:

I thought this was going to go off without a hitch... but I suppose not. The SATA drive was DOA (THANKS SEAGATE). Fast forward...
To the comments...[11:04:18 2006-10-30] <+Toba> 11:04:18 up 22 min, 9 users, load average: 3.67, 2.86, 1.52
[11:04:42 2006-10-30] <+Toba> meh, it's just my desktop
[11:04:45 2006-10-30] <+Toba> but that was fracking weird
Little did I know that my UPS's battery failure was not just annoying, it was deadly to motherboards. I blithely continued watching season 4 of Stargate SG-1, thinking I'd solved the problem by replacing my power strip, heaven forbid my UPS could *cause* problems.[11:04:42 2006-10-30] <+Toba> meh, it's just my desktop
[11:04:45 2006-10-30] <+Toba> but that was fracking weird
[23:58:16 2006-11-01] <+Toba|BSD> aghlaghalghalhglahlaghlagh
I'm pretty sure you can figure out what that means. Yeah, happened again, but this time the system won't boot at all. So I replaced my motherboard with a random one from my closet.[15:33:41 2006-11-02] <+Toba> oh, and my cpu and ram being way slower
[15:33:52 2006-11-02] <+Toba> this is a good excuse to replace all my hardware
I didn't have any money to buy new stuff right away, so I kept on trucking...[15:33:52 2006-11-02] <+Toba> this is a good excuse to replace all my hardware
[12:45:47 2006-11-04] <+Toba> diff motherboard
[12:45:53 2006-11-04] <+Toba> that is causing my system to randomly reboot
[12:45:59 2006-11-04] <+Toba> and underclocking my cpu and ram by a ton
Later, in reference to something Ken was doing:[12:45:53 2006-11-04] <+Toba> that is causing my system to randomly reboot
[12:45:59 2006-11-04] <+Toba> and underclocking my cpu and ram by a ton
[23:51:24 2006-11-04] <+Toba> a hard drive is about to get hammered
I continue to try to debug my hardware problems, oblivious to my approaching doom.[16:34:08 2006-11-05] <+Toba> I just spent an 2.5 hours trying to fix this
[16:34:11 2006-11-05] <+Toba> and right after I boot
[16:34:14 2006-11-05] <+Toba> gnome dies
[16:34:11 2006-11-05] <+Toba> and right after I boot
[16:34:14 2006-11-05] <+Toba> gnome dies
[23:15:00 2006-11-06] <+Toba> my taskbar is broken
[23:15:03 2006-11-06] <+Toba> but I can still alt tab
[23:15:03 2006-11-06] <+Toba> but I can still alt tab
Failure
At about noon the next day my system crashed hard and corruped partition tables and superblocks on both drives. Grub couldn't find my kernel and Knoppix couldn't mount anything.At this point, I still had no money and now no computer. My paycheck was still a ways off. So, I stumbled along with my laptop for a few weeks. By the way, said laptop's window manager killed itself violently when I used portupgrade, so I was using TWM. TWM sucks. TWM sucks more than you can possibly imagine. It's ugly, it has the bare minimum of functionality, and did I mention that it's ugly? Behold, how ugly it truly is:

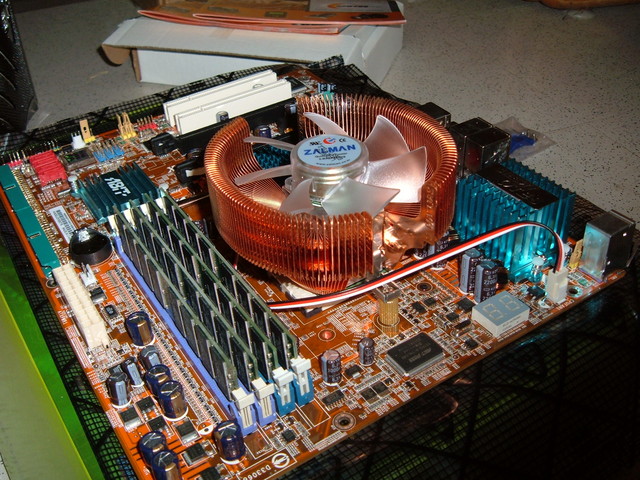
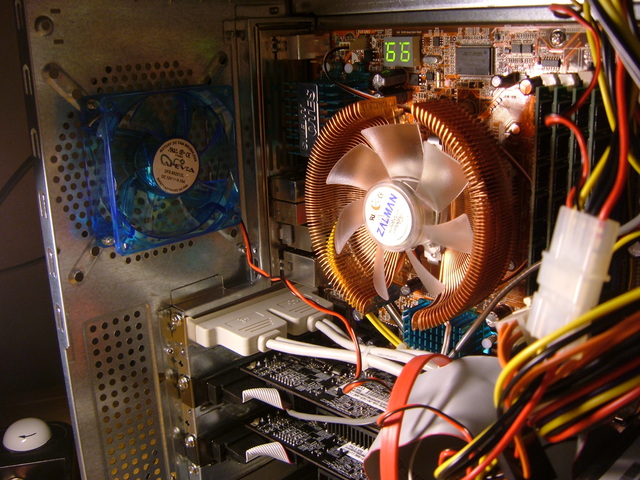
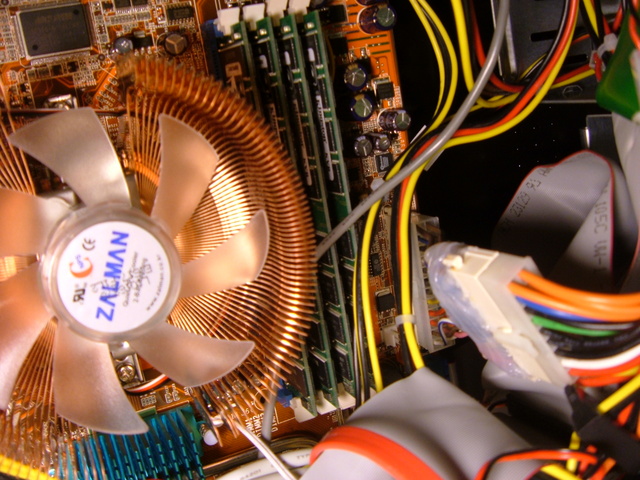
New parts
I spent a total of $970 on:- Apevia ATXB8KLW-BK Case
- Abit AN8 32X Motherboard
- XFX GeForce 6200TC Video cards (2)
- 2 DVI to VGA adapters
- AMD Athlon64 X2 4400+ CPU
- 2x512MB PC3200 Kingston RAM
- 80GB Seagate SATA 3gb/s HDD
- Microsoft Natural Keyboard
- Samsung DVD/CD Writer
- Zalman CNPS7000B-CU Copper HSF
I thought this was going to go off without a hitch... but I suppose not. The SATA drive was DOA (THANKS SEAGATE). Fast forward...
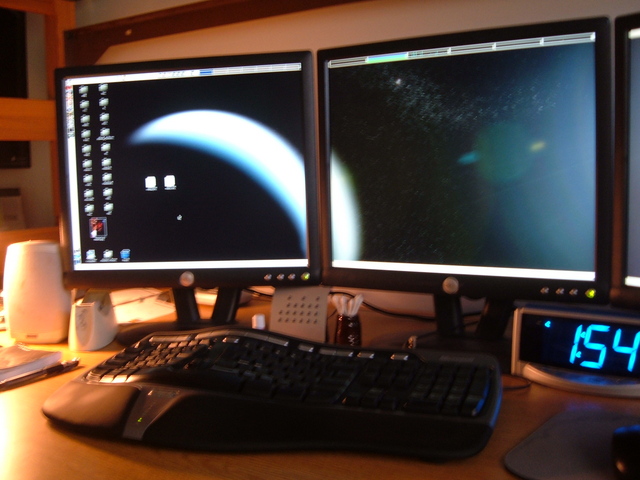
AWESOME.
3840x1024, baby.Pings, pongs, proxies, and privacy
Posted by Eric Stein - November 13, 2006 CE @ 21:09:38 UTC
What if I told you that using the IP of your phone I could track your movements to a certain extent? If I knew when you stopped moving? How solid the building you're in is?
Well, I'm telling you. I think you can interpret this un-tampered with data (minus the IP, of course) for yourself.
Stationary, inside a wood frame building:
It's all in the variance. You might want to firewall your cellphone.
To the comments...
Well, I'm telling you. I think you can interpret this un-tampered with data (minus the IP, of course) for yourself.
Stationary, inside a wood frame building:
64 bytes from x.x.x.x: icmp_seq=1 ttl=237 time=212.818 ms
64 bytes from x.x.x.x: icmp_seq=2 ttl=237 time=216.064 ms
64 bytes from x.x.x.x: icmp_seq=3 ttl=237 time=220.900 ms
64 bytes from x.x.x.x: icmp_seq=4 ttl=237 time=196.416 ms
Walking accross campus:64 bytes from x.x.x.x: icmp_seq=2 ttl=237 time=216.064 ms
64 bytes from x.x.x.x: icmp_seq=3 ttl=237 time=220.900 ms
64 bytes from x.x.x.x: icmp_seq=4 ttl=237 time=196.416 ms
64 bytes from x.x.x.x: icmp_seq=79 ttl=237 time=220.914 ms
64 bytes from x.x.x.x: icmp_seq=80 ttl=237 time=2332.255 ms
64 bytes from x.x.x.x: icmp_seq=81 ttl=237 time=1348.074 ms
64 bytes from x.x.x.x: icmp_seq=82 ttl=237 time=360.149 ms
Stationary, inside a brick library:64 bytes from x.x.x.x: icmp_seq=80 ttl=237 time=2332.255 ms
64 bytes from x.x.x.x: icmp_seq=81 ttl=237 time=1348.074 ms
64 bytes from x.x.x.x: icmp_seq=82 ttl=237 time=360.149 ms
64 bytes from x.x.x.x: icmp_seq=156 ttl=237 time=375.544 ms
64 bytes from x.x.x.x: icmp_seq=157 ttl=237 time=385.727 ms
64 bytes from x.x.x.x: icmp_seq=158 ttl=237 time=395.610 ms
64 bytes from x.x.x.x: icmp_seq=159 ttl=237 time=385.113 ms
64 bytes from x.x.x.x: icmp_seq=157 ttl=237 time=385.727 ms
64 bytes from x.x.x.x: icmp_seq=158 ttl=237 time=395.610 ms
64 bytes from x.x.x.x: icmp_seq=159 ttl=237 time=385.113 ms
It's all in the variance. You might want to firewall your cellphone.